Digital security no longer revolves solely around encryption and firewalls. While encryption secures information by transforming it into unreadable formats, the very presence of encrypted content often raises suspicion. Governments, corporations, and malicious actors may notice its existence, prompting further investigation. This makes it necessary to develop techniques not only for protecting data but also for concealing its existence altogether.
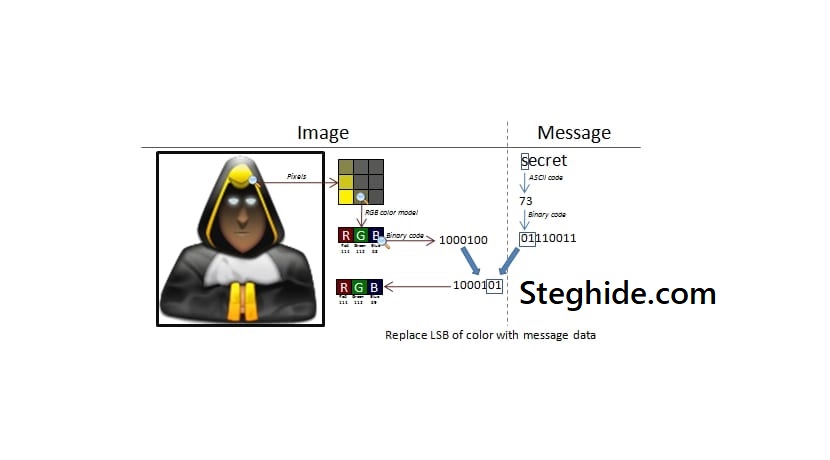
This is where steganography enters. By hiding data inside ordinary-looking files such as images or audio, steganography creates covert communication channels. One of the most practical, open-source, and widely recognized tools for implementing steganography is Steghide. Available on multiple platforms, it empowers users with efficient and discreet methods of embedding sensitive files.
Central to Steghide’s functionality is its command syntax, a structured format that directs the software in embedding or extracting data. Understanding how to use this syntax properly is essential for security professionals, researchers, students, and everyday users seeking privacy. This guide unpacks Steghide’s syntax in depth, covering basics, advanced parameters, step-by-step execution, practical examples, pros and cons, and comparisons with alternative tools.
Steghide Command Syntax
Basic Structure
At its core, Steghide follows a simple command format for embedding:steghide embed -cf [coverfile] -ef [embeddedfile] -p [passphrase]
Here, the carrier file is the ordinary-looking medium, the embedded file contains hidden data, and the passphrase secures the extraction. Following this syntax ensures operations succeed smoothly without altering carrier usability.
Role of Flags
Flags provide specific instructions to Steghide. The -cf flag identifies the carrier, -ef pinpoints the hidden file, and -p assigns the password. Without correct flag usage, commands either fail or produce flawed results. Understanding each flag’s function equips users with complete control over embedding operations.
Practical Syntax Example
Suppose a user wishes to hide secret.txt inside image.jpg. The correct syntax is:steghide embed -cf image.jpg -ef secret.txt -p mypassword
This creates a visually identical image file containing concealed text accessible only through the designated passphrase.
Breaking Down Embedding Parameters
Carrier File (-cf)
The carrier file represents the visible medium used to host secret content. Supported formats include JPEG, BMP, WAV, and AU. File size matters: larger carriers allow more data without detectable distortion. Choosing an appropriate carrier improves stealth and reduces detection risks.
Embedded File (-ef)
The embedded file contains sensitive information to hide. It may be a document, binary executable, or compressed archive. Before embedding, Steghide compresses the content to optimize efficiency. Compression reduces redundancy and ensures the carrier retains its original appearance or sound quality.
Passphrase (-p)
The passphrase protects access to hidden data. Without the correct key, extraction becomes impossible, even if someone suspects steganography. Strong passphrases combine length, complexity, and unpredictability. Effective use of the -p option strengthens data confidentiality while complementing the concealment layer.
Advanced Options for Embedding
Quality Factor (-q)
The -q flag adjusts the quality of JPEG carriers. Higher quality reduces embedding capacity but maintains visual fidelity. Lower quality increases available storage but may slightly degrade image clarity. Striking a balance ensures both discretion and capacity, depending on user needs.
Encryption Algorithm (-e)
Steghide defaults to AES encryption, but the -e option lets users specify alternatives. Supported algorithms depend on system libraries. Selecting algorithms with strong resistance to brute-force attacks enhances resilience. This option empowers professionals to align security measures with organizational policies.
Overwriting Hidden Data (-Z)
The -Z flag allows overwriting pre-existing embedded content within a carrier. This ensures reusability of media files without clutter or conflicts. However, users must exercise caution, since overwriting eliminates previously hidden data permanently. Proper planning avoids unintentional data loss.
Step-by-Step Usage Guide
Preparing the Environment
Before embedding, gather both the carrier and the secret file in one directory. Confirm carrier file compatibility and ensure sufficient size relative to the secret. Avoid repeatedly editing or compressing the carrier, since post-embedding alterations can corrupt hidden data.
Executing Embedding Commands
Embedding follows this structure:steghide embed -cf [carrier] -ef [secret] -p [password]
-cfdefines carrier-efspecifies embedded file-psecures access
Execution produces a stego-file outwardly identical to the original carrier yet harboring concealed content.
Verifying Embedded Content
After embedding, Steghide confirms successful execution. Users may inspect carriers to verify functionality remains intact. Attempting extraction with the steghide extract command validates hidden content accessibility, confirming embedding accuracy.
Practical Examples of Steghide Syntax
Embedding Text Files
For hiding a text file named credentials.txt inside an image cover.jpg with password key123, the syntax is:steghide embed -cf cover.jpg -ef credentials.txt -p key123
This generates a new stego-image indistinguishable from the original yet containing sensitive login data.
Hiding Binary Applications
Embedding an executable into an audio file may involve:steghide embed -cf sound.wav -ef app.exe -p lockpass
The resulting file remains playable while securely storing the application. This showcases Steghide’s versatility in handling diverse file types.
Concealing Documents for Privacy
To hide private financial records report.docx inside family.bmp:steghide embed -cf family.bmp -ef report.docx -p strongsecret
The BMP image appears unaltered but safely conceals confidential financial data, ensuring discreet protection.
Advantages and Limitations of Syntax Usage
Benefits of Command Syntax
- Precision: Direct control over embedding operations
- Security: Combination of concealment and encryption
- Efficiency: Lightweight and fast execution
- Cross-Platform Support: Works on Linux and Windows
- Open Source: Free and modifiable for customization
Possible Drawbacks
Despite strengths, syntax usage requires accuracy. Errors in command structure produce failures. Carrier support remains limited to a few file types. Embedding excessive data risks detection due to file anomalies. Users must balance capacity with subtlety.
Ethical Responsibility
Steghide offers immense power. Responsible application safeguards privacy and intellectual property. Misuse, however, may enable harmful activities. Users must follow legal frameworks and ethical standards, applying Steghide solely for constructive purposes.
Comparing Steghide Syntax with Other Tools
Steghide vs SilentEye
SilentEye provides a graphical interface for simplicity, appealing to beginners. However, Steghide’s syntax grants advanced users finer control, stronger encryption integration, and flexibility for automation through scripting. Professionals prefer syntax for reliability in security tasks.
Steghide vs OpenStego
OpenStego emphasizes watermarking alongside data hiding, offering broader use cases. While easier for non-technical users, OpenStego lacks the granular control Steghide’s syntax provides. Professionals requiring command-level precision typically choose Steghide.
Steghide vs OutGuess
OutGuess expands compatibility with more carrier formats, but Steghide ensures stronger cryptographic pairing. Syntax options within Steghide grant detailed customization, appealing to users prioritizing encryption. Choice depends on whether breadth of formats or cryptographic resilience is more important.
Real-World Applications of Steghide Syntax
Cybersecurity Defense
Organizations employ Steghide syntax for covertly sharing sensitive strategies. Executives can embed critical plans in innocuous images, ensuring private communication beyond traditional encryption. This extra concealment layer strengthens resilience against corporate espionage.
Digital Forensics
Investigators use Steghide to detect or replicate techniques employed by criminals. Understanding syntax equips forensic teams with the knowledge to uncover evidence hidden in media files, enabling law enforcement to track digital crimes effectively.
Individual Privacy
Individuals protect diaries, legal files, or confidential communications using Steghide syntax. By embedding them into ordinary media, personal data remains private while avoiding detection. As online risks increase, syntax-driven steganography becomes a vital privacy shield.
Conclusion
Mastering Steghide’s command syntax is essential for harnessing the full potential of steganography. By combining concealment with strong encryption, commands like -cf, -ef, and -p enable efficient and secure embedding. Advanced options enhance flexibility, while examples highlight versatility across text, binaries, and documents. Although limitations exist, responsible application ensures benefits outweigh drawbacks. In a digital era dominated by surveillance and threats, Steghide’s syntax offers a powerful yet discreet method of protecting sensitive information.